 January 23, 2022 - BY Admin
January 23, 2022 - BY Admin
Nexsan
ASSUREON® ACTIVE DATA VAULT OVERVIEW
The Nexsan Assureon® active data vault solution is ideal for any organization that needs to protect data and backups from cyberattacks and ransomware, implement regulatory and corporate compliance, long-term archiving of unstructured data, or storage optimization. Users do not need to learn anything new, change how they access data or learn any new processes.
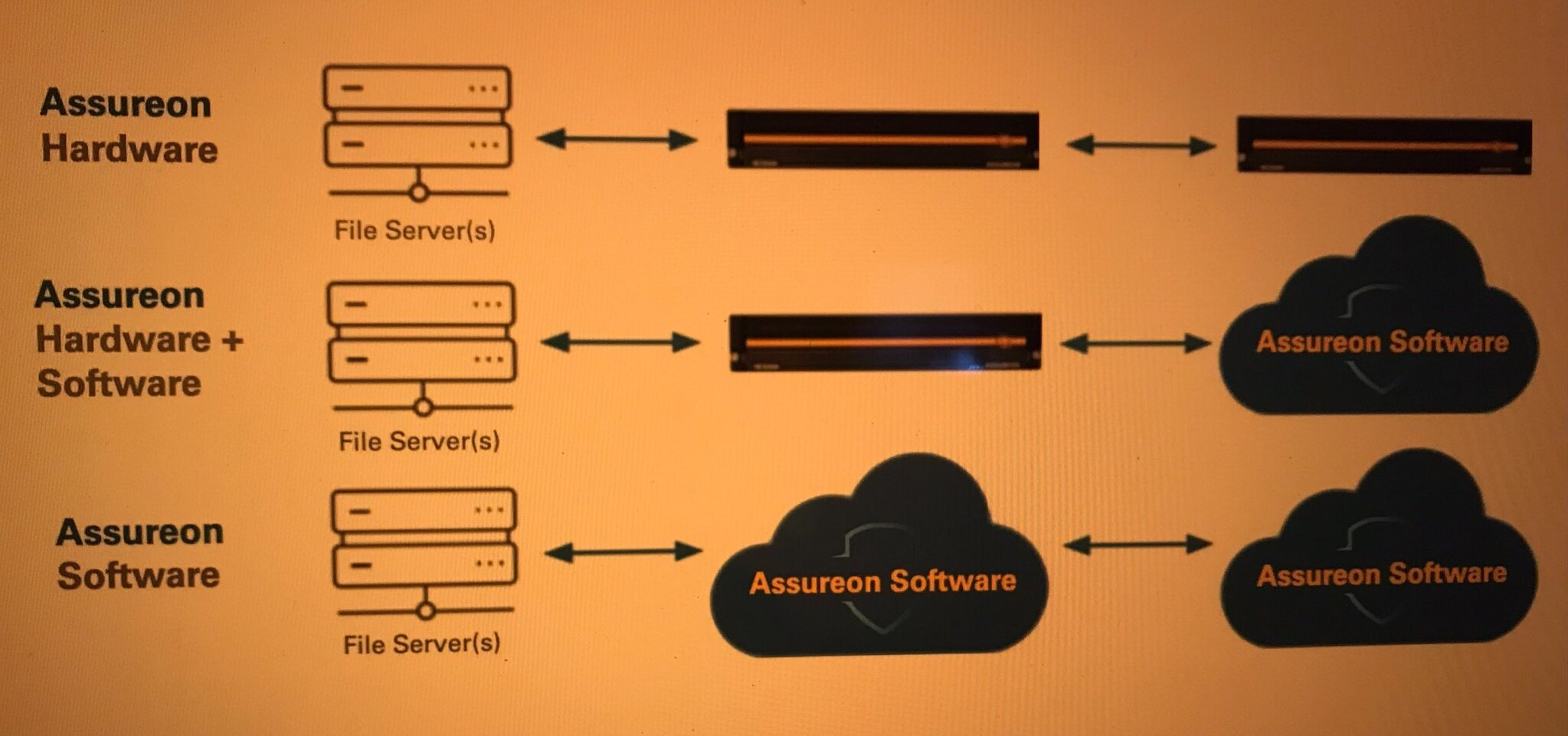
Assureon’s unique file fingerprinting and asset serialization process, in conjunctio with metadata authentication, private blockchain and a robust data verification algorithm, securely protects your digital assets. Data stored in the Assureon is immutable and cannot be corrupted by malicious malware. Assureon can be deployed as a software or hardware appliance. Both deployment options deliver all the unique data protection benefits to protect unstructured data and backups from cyberattacks, user error, and also meets regulatory compliance requirements.
ASSUREON SOFTWARE
Assureon Software gives you the flexibility of selecting a deployment option that best fits your organization’s infrastructure strategy. Assureon software can be implemented in a public cloud or on-premise. The software can be deployed on any standard or virtualized server.
UNBREAKABLE BACKUP
As malware is now also targeting backups, Assureon, in conjunction with UnityTM, provides the last line of defense to protect backups from any malware,
ransomwa NEXSAN.COM re attacks, or user error so organizations can recover backups from a worst-case scenario.
REGULATORY AND CORPORATE COMPLIANCE
Assureon complies with the toughest governmental regulatory requirements including HIPAA, GDPR, CCPA, GLBA, Sarbanes-Oxley, Federal Rules of Civil Procedure
(FRCP), CJIS, SEC 17A-4 and PCI DSS. Additionally, Assureon makes it easy and automatic for organizations to adhere to their internal guidelines for data retention, deletion, privacy, protection and risk mitigation. Assureon exceeds even the strictest regulatory requirements for data integrity, protection, privacy, security, longevity and availability with full audit trails.
ENTERPRISE FEATURES
|
Failover/Failback |
Native active/active replication protects against site disasters with automatic read failover and manual write failover. |
|
Performance |
Optional RoCE (RDMA over Converged Ethernet) connectivity delivers blazing-fast 40GbE read functionality for virtual shortcuts. |
|
Private Blockchain |
Protect and secure digital assets with the immutable data structure utilizing cryptography to secure transactions. Automated integrity audits and redundant sites maintain data integrity and transparency. |
|
Regulatory Compliant |
Assureon complies with governmental regulatory requirements including HIPAA, GDPR, CCPA, GLBA, Sarbanes-Oxley, Federal Rules of Civil Procedure (FRCP), CJIS, SEC 17A-4 and PCI-DSS. |
|
Geographic Separation |
Two active Assureon systems can continuously replicate to each other to protect against site (cloud) outage. |
|
Scalable Capacity |
Scale capacity up to multiple petabytes and add performance by using multiple Assureon archive storage systems together. All nodes across sites are managed through a seamless management interface. |
|
Storage Optimization |
Transparently offload inactive unstructured data from Tier-1 or cloud storage for a more cost effective solution that’s easily retrieved. |
|
Unbreakable Backup |
Assureon protects from ransomware attacks and can be implemented in various configurations including tiered, replicated and high availability. |
DATA INTEGRITY
|
Chain of Custody |
Self-healing integrity checks and file availability audits along with digitally signed metadata files and third- party secure time stamps work together for the utmost protection of files within Assureon. Together, this applies a verifiable chain of custody to each data set throughout the retention period. |
|
Data Verifi ation |
Files are continually verified against their fingerprints, repaired using their copies and safeguarded by RAID disk arrays for days or decades. |
|
Fingerprints |
Each time a file is saved, a unique fingerprint is generated using both an MD5 and SHA1 hash of its contents and metadata, so history and contents cannot be altered after the fact (WORM storage). |
|
Secure Time |
Tampering with the system time clock is prevented by using a global, redundant, secure time source. |
|
File Audit |
Each file is assigned a serial number which is used to ensure no files are missing or inappropriately added. |
|
Two Copies |
Each file and its fingerprint is stored twice in the Assureon. The second copy is either stored in a separate RAID disk set in the same Assureon or on a remote Assureon. |
ABOUT NEXSAN, A STORCENTRIC COMPANY
Nexsan® is a global enterprise storage leader since 1999 delivering the most reliable, cost-effective and highly efficient storage solutions. Nexsan’s solution portfolio empowers enterprises to securely store, protect and manage valuable business data with a broad product line of all-flash NVMe, unified storage, block storage, and secure archiving. Nexsan is a proud member of the StorCentric Family. www.nexsan.com